Mobile Device Security is a pattern of policies, strategies and tools set in place to fortify mobile devices from virtual security threats. It seeks to secure the sensitive information stored or carried by t,+hese devices from duplication or malware.
The need for Mobile Device Security of each enterprise may vary from company to company. It primary objective of such security measures to prevent unauthorized access to a business network by means of authentication and restriction. Without the installation of appropriate security, it is hard for enterprises to determine if their mobile data is secure.

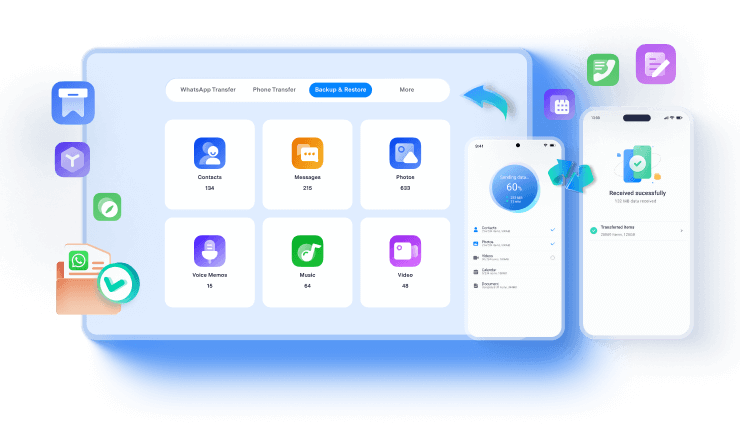
Part 1: How to Transfer Data from Samsung to Vivo Directly via MobileTrans
1.1 What is Mobile Data Security?
A strategy that is comprised of techniques and software which secure a device from any malware attacks or cyber threat can be seen as aligned with Mobile Device Security. More than 50 percent of all business enterprises are dependent on a network of mobile devices such as smartphones and wireless PCs. By further adding the Internet of Things (IoT) to the mix there is a rapidly growing need to enhance a business’s approach towards Mobile Device Security.

1.2 Key Elements to the Functioning of Device Security
To establish security over a company’s mobile device network each organization needs to administer multiple layers of approach by investing strategies and solutions. Although there are a few key elements involved, each enterprise would need to leverage a tailored approach to their security requirements.

- Enforcing clearly defined Policies and Processes
Rules and policies put in place by a company are only as effective if they are appropriately communicated. This communication should include;
- The objective of a device.
- Levels of OS accessible by employees.
- Limits of company’s access to a personal device.
- If remote wiping of devices is actionable by IT.
- Frequency of updating passwords.
- Password Diversity
At the base of preventing any unauthorized entry into a network is the ‘password’. Weak passwords lead to an increase in data hacks. It is imperative for employees to use different passwords for each of their company-related accounts. These passwords should be minimum eight character strong and unique each time.
- Biometric Access
A safer and more reliable alternative to passwords is the installation of biometrics. This involves authenticating biological features of an employee including fingerprint, voice, facial recognition or iris recognition. Multiple biometrics authentication is now processes are now available on smartphones and other devices, and can be easily set up by employees or workers.
- No Public Wi-Fi
Convenience is the death of stability, in this case mobile device security. It is the responsibility of a business organisation to educate users on the perils of using public Wi-Fi networks and how hackers can gain access and steal data without them knowing. Smartphone data usage should be encouraged over the need for reverting to free public data networks.
- App Danger
There are millions of malicious apps available for download which presents a great security threat to a company’s network. Downloading such apps can trigger unauthorized access to a company’s data structure. Therefore, organisations can take measures such as educating employees on avoiding such apps or banning the download of certain types of apps on personal devices.
- Device Encryption
Smart devices which are available on the market today are all equipped with encryption features. These features are highly useful as they convert data into code which can only be decrypted by authorized personnel, ensuring the security of such data.

- Different Protection Measures in Mobile Device Security

Commonly known approaches to achieving complete Mobile Device Security are enlisted below;
- Enterprise Mobile Management (EMM)
It is important companies to take all possible measures to ensure that their network of personal devices is not susceptible to cyber threats, but in order to do it is essential to set an Enterprise Mobile Management platform. This would enable IT admins to gain valuable insight that would help them identify threats way beforehand.
- Email Security
Employee Emails are a prime portal for malware and ransomware to gain entry into a network. In order to establish immunity against such attacks, businesses need to apply critical email security measures that are armed to detect, address and block threats before they can cause damage. This involves faster prevention of data loss through end-to-end encryption measures.
- Protecting Endpoints
Loosely protected endpoints enable security threats to remotely access mobile devices. Efficient endpoint security ensures standardization of security policies which alerts IT admins on the detection of threats and dealing with them before any damages take place. It also facilitates the monitoring of endpoint operations and backup strategies.
- Virtual Private Network
VPN’s function as an extended private network over a public network. This means, users can send or receive information from a public network while virtually imitating a private network. Also, VPN encryption facilitates a secured access to corporate networks and application.
- Protected Web Gateways
Cloud based networks are rapidly emerging therefore it has become imperative to enforce security policies that defend against malware and phishing in real time. Effectively securing web gateways would enable the detection of attacks and threats at one gateway and immediately administer a counter measure to protect all other gateways.
- Security Access Broker
Cloud Access Security Broker or CASB can be perceived as a layer of protection placed between cloud service consumers and providers. This tool enforces compliance, governance and security over cloud applications which protects that infrastructure of the cloud platform.
Part 2: Why is Mobile Device Security Important?
Portable Mobile Devices like wireless PCs and smartphones are being used by 90% of the employees of any organization. When these devices are linked into the company’s system data network they present a substantial security threat if not properly checked.
Large corporates are targeted by cyber criminals for extracting sensitive information or to extort money by means of phishing scams, malicious apps, data leaks, spyware and unreliable Wi-Fi networks. There is also the underlying risk of employees losing their devices. These dangers pose a risk because individuals do not practice safe habits of cyber security such as setting multiple layers of security or enabling password protection.

In order to enhance mobile device security in an organization against any malicious threats appropriate security procedures can be partnered up with a reliable EMM platform along with other applications of network security to facilitate remote management by the IT department. Achieving this level of capability can potentially increase security for a network as IT administrators can remotely wipe company data from any lost devices, administer updates, detect stolen devices and much more. Securing mobile devices although is not a simple to achieve goal. Then again it should be on the top of all enterprises.
Part 3: What Are the Benefits of Mobile Device Security?
Real-time Protection: Administering a mobile device security solution would enable your network to remain secure from cyber threats 24/7. IT administrators would be able to identify and prevent malware infiltration in real-time. It is important to remain protected from such risk since the damages to your data can be of great significance.
Browsing Security: Browsing is essential for all wireless devices as that is how information is carried around. With the prevalence of the internet of things (IoT) it is essential to keep mobile device browsing safe from cyber threats. By establishing Mobile Device Security, businesses are able to keep their security standards at its best while protecting devices from web attacks.
Enhanced Device Performance: More companies are adopting a BYOD company structure therefore there is the increased need for Mobile Device Security to prevent network attacks by hackers and scammers. There is also the need for keeping track of devices in case of mobile devices have gone missing. It promotes mobile access to such devices as well as automation in terms of registration and backup.

Key Takeaways from This Episode
- It is easy enough to understand that Mobile Device Security is crucial to keeping an enterprise network safe and functioning.
- It is not easy to maintain but it is definitely more than worth the effort and investment as cyber threats are always up and about.
- It is essential to keep cyber security methods up to date at all times as malware and spyware are always evolving in to more advanced forms.
New Trendings
Top Stories
All Categories









Nicola Massimo
staff Editor